How to manually grant tenant-wide admin consent to Gizmo
CLOUD ON-PREMISES
Applies to Gizmo 1.7+
This article describes how to grant consent to Gizmo application in your tenant, on behalf of your entire organization, even before your Gizmo environment is provisioned.
Instructions
This reflects the best practices and requirements as exposed to Microsoft here: https://docs.microsoft.com/en-us/azure/active-directory/manage-apps/grant-admin-consent
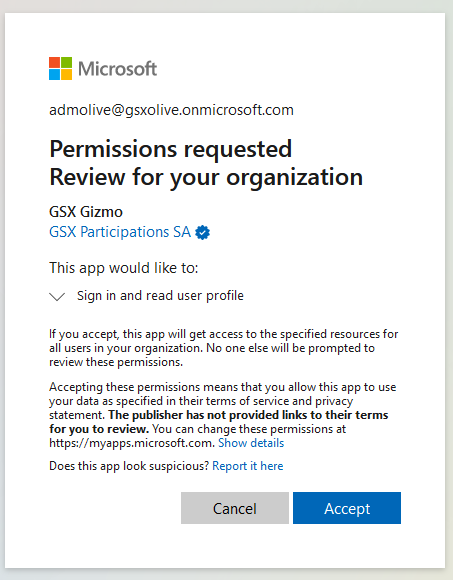
In order to grant consent, the user must be authorized to “consent on behalf of the organization”, and can use the following URL: https://login.microsoftonline.com/{tenant-id}/adminconsent?client_id={client-id}
To build this URL you need:
Your tenantID, which can be obtained through the following PowerShell line:
(Invoke-WebRequest https://login.windows.net/YOUROFFICE365DOMAIN.onmicrosoft.com/.well-known/openid-configuration|ConvertFrom-Json).token_endpoint.Split(‘/’)[3]
A Gizmo ClientID: bc8efea5-2a0d-4181-ad8f-f0aa5b7cb525
Therefore the URL which should be opened with the required permissions should look like:
The following steps should then take place:
Login with your Azure AD administrator account (or user with authorized “grant consent on behalf of organization).
Accept the “grant consent”.
You will be then redirected to a non existing page. This is an expected behavior.
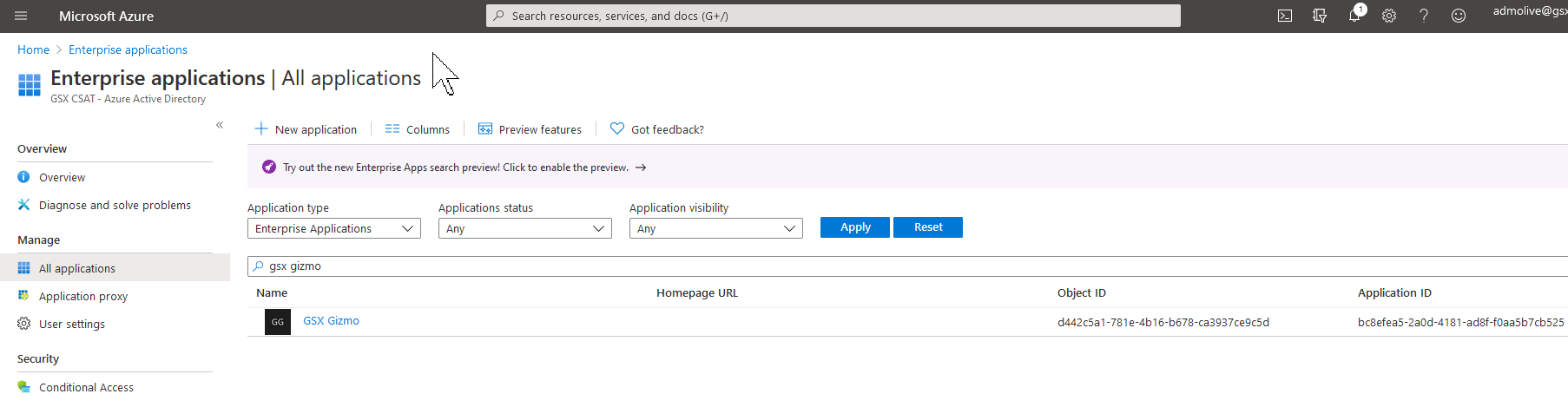
Ensure in the Azure AD admin portal that there is now an Enterprise Applications named “GSX Gizmo”: